Tips on Configuring and Using Windows Firewall in your VPS and Dedicated Server
A question that’s been coming up rather often lately is: “How do I configure the Windows Firewall on my Dedicated Server / VPS Server?” Not many people realize that in SP1 Windows 2003 got a software firewall feature added and even fewer are familiar with how to configure it correctly. Because of this I wanted to provide a few tips on how to configure your Windows Firewall. Please note that this is NOT the all encompassing tutorial on how to secure your server or how to use Windows Firewall but it’s a great starting point.
Introducing the Windows Server 2003 Firewall
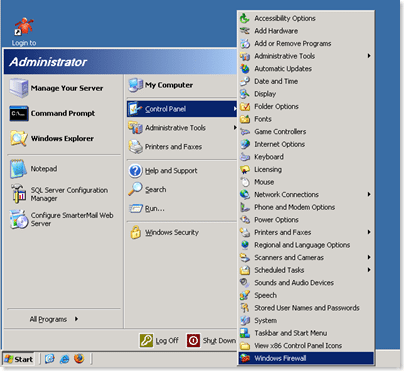
Many people are aware that Windows Server 2003 has a GUI for the firewall. You can access it from the start menu as shown below:
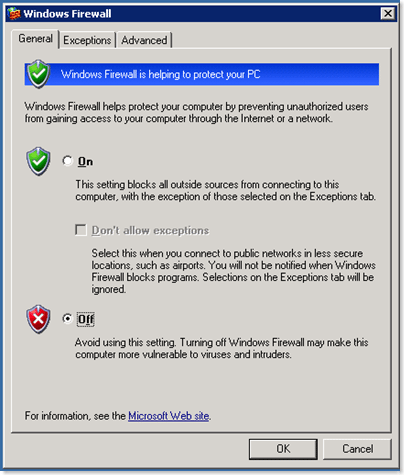
When you first click that icon it’s going to enable Windows firewall and present you with a nice GUI and if you’re not careful you’ll proceed to get yourself in a lot of trouble!
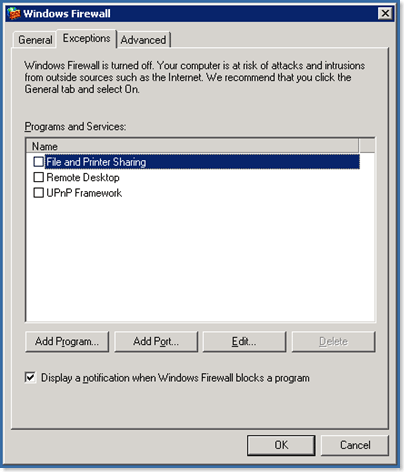
I really don’t advise you configure Windows Firewall from the GUI, atleast initially. The reason for this is if you go to exceptions you’ll only get a few options:
Sure you can enable an Exception for Remote Desktop but what about IIS, DNS, maybe Mail? In fact, the most common support question regarding Windows Firewall is “I turned on Windows Firewall and now I can’t connect to my server via Remote Desktop any more, HELP!” It happens 🙂
Thus enters the Command Line Interface (or CLI as we like to call it).
Managing the Windows Firewall via CLI
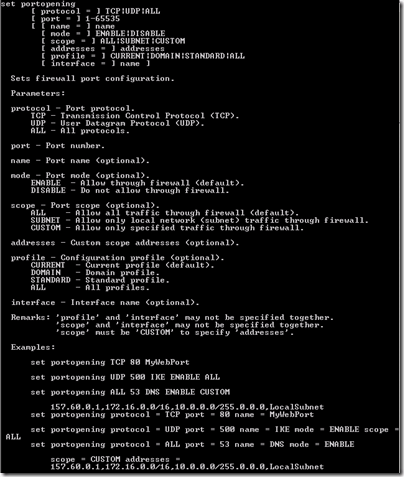
The real beauty of configuring the Windows Firewall via CLI is that you have much more control over it. In fact if you open a dos window and type: netsh firewall set portopening
you’ll get output like this:
Which provides all the gory details on how to configure the Windows Firewall port openings. A few things about the Windows Firewall in Windows Server 2003,
1. you can only block inbound packets (you have no control over outbound packets, that is available in Windows Server 2008 though).
2. In a normal firewall you can block a port for specific IPs. So let’s say you’re getting attacked on port 80 from 10.5.5.5 you can block that IP on just that port. You can’t do this with Windows Firewall In 2003. So with Windows Server 2003’s firewall you can do the following with a port:
- a. block it for everyone from the outside
- b. allow it open for everyone from the outside.
- c. allow it open for only certain IP addresses.
That’s the bad news, that’s really all we have to work with, the good news is in Server 2008 so much more is available and I’ll blog about that later.
If you want a full list of what you can do, you can go to this article on technet:
Windows Firewall Tools and Settings (server 2003)
Windows Firewall Tools and Settings (server 2008)
The AppliedI Quickie Firewall Ruleset
In an earlier blog post on the AppliedI blog, I spoke about Joe Healy and mentioned a little cookbook of firewall rules I like to enable on my own personal VPS servers. These rules are here:
1: netsh firewall set opmode enable
2: netsh firewall set portopening TCP 80 HTTP
3: netsh firewall set portopening TCP 53 DNS-TCP
4: netsh firewall set portopening UDP 53 DNS-UDP
5: netsh firewall set portopening TCP 21 FTP-Server
6: netsh firewall set portopening TCP 220 IMAP3
7: netsh firewall set portopening TCP 143 IMAP4
8: netsh firewall set portopening TCP 25 SMTP
9: netsh firewall set portopening TCP 110 POP3
10: netsh firewall set portopening TCP 3389 RDP
11: netsh firewall set portopening TCP 443 HTTPS
12: netsh firewall set portopening TCP 9999 SmarterMail
13: netsh firewall set portopening TCP 9998 SmarterStats
14: netsh firewall set logging droppedpackets=enable
Line #1 turns on the firewall. Lines #2-13 enable various port openings for all IP Addresses and Line #14 enables logging.
The only caveat I’ve run into this set of rules is that passive FTP no longer works as a result of this change. The workaround for this is to enable Passive FTP on a given set of ports and then open these ports in the firewall as well. Here’s a KB article on how to do this. You’ll also want to open these 100+ ports on the firewall and here’s a little code (from here) on how to do that:
To add a range of ports to Windows Firewall from the Command Line
- Click Start, click Run, type cmd, and then click OK.
- Type in the following where the range is specified in ( ) and the name of the firewall entry is in ” “.
FOR /L %I IN (5001,1,5201) DO netsh firewall add portopening TCP %I “Passive FTP”%I - Each port in the range will be added with an “OK” confirmation.
This opens more ports than you’ll probably need and you can adjust these accordingly.
Opening a Port for a specific IP Address
A fairly common request we get is how do I open a port for only specific IP addresses and block it for everything else. This comes when a user wants to open port 1433 to their SQL Service so they are able to access it remotely using SQL Management Studio but leave it closed to the rest of the world.
Let’s assume we want to open PORT 1433 for TCP requests only and only to the IP address 10.5.5.5 the way to do that is with this CLI command:
1: netsh firewall set portopening protocol=TCP port=1433
name=MySQLAccess mode=ENABLE scope=CUSTOM addresses=10.5.5.5
This opens that port for a custom scope of addresses which in this case is only 10.5.5.5
What else can I do?
Well, there’s a lot more you can do with Windows Server 2003’s Firewall and this really just scratches the surface on what can be configured and how. Many people complain a software firewall is not a good firewalling solution because if a hacker can get into your server they can disable it or do what they wish to it. But I believe the added layer of security a software firewall brings to the table in addition to other network security features in place (such as network firewalls, IPS, IDS, etc) that it’s only wise to run it as well.